The Role of Private and Public Keys

With the rise in adoption of bitcoin, understanding the underpinnings of public and private keys becomes essential. This blog post offers an in-depth look into these keys, exploring their role, generation, usage, and the importance of their secure storage.
What is a Bitcoin Private Key?
In Bitcoin, a private key is an elaborate string of 256-bit numbers. It holds paramount importance, serving as the exclusive password that permits a Bitcoin user to access and transact with their unspent transaction outputs (UTXOs). It functions as the ultimate proof of Bitcoin ownership, its value becoming pronounced considering the irreversible nature of Bitcoin transactions.
How Do Private Keys Function?
Bitcoin security hinges on an encryption system known as public key cryptography. Herein, each Bitcoin address aligns with a distinctive public key and a private key. The public key behaves as the equivalent of a Bitcoin receiving address, while the private key permits the Bitcoin's spending.
Interestingly, the public key isn't chosen randomly. It is calculated from the private key through a mathematical function. This function is unidirectional, that is, it can only go from the private key to the public key, and not the other way around. Consequently, your Bitcoin remain secure as long as your private key is kept secret, even if your public key is in plain sight.
How are Private Keys Generated?
The generation of private keys typically falls within the purview of a Bitcoin wallet like Theya. When a new wallet is set up, the software spawns a random private key, ensuring its uniqueness. The wallet then securely stores the key within its database, keeping it ready for transactions and securing it from unauthorized access.
More technical explanation: The private key, a unique 256-bit long number, is produced using a cryptographically secure pseudorandom number generator (CSPRNG). These generators are designed to be unpredictable and resistant to cryptographic analysis, ensuring that every generated private key is unique and almost impossible to replicate or predict.
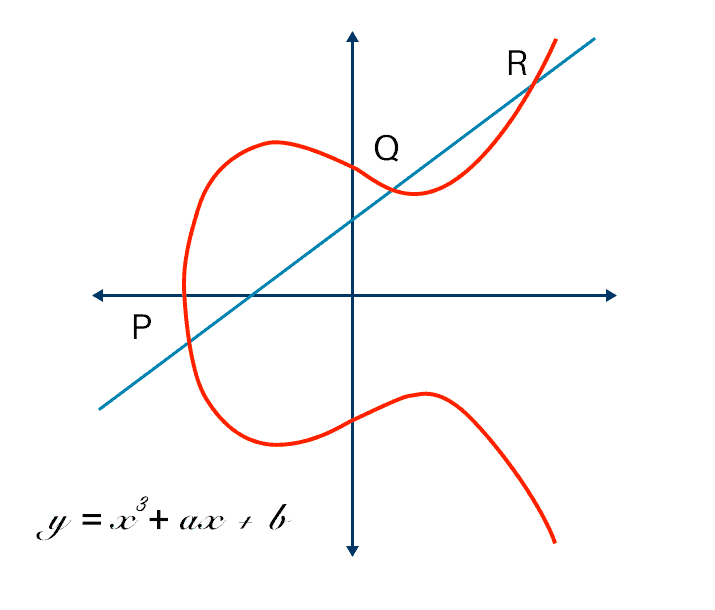
Post-generation, the wallet employs the Elliptic Curve Digital Signature Algorithm (ECDSA) over the secp256k1 curve, a set of cryptographic standards, to derive a public key from the randomly generated private key. The derived public key forms the basis for the Bitcoin address, which is essentially a hashed version of the public key. It's crucial to note that while the public key can be easily computed from a private key, reverse-engineering a private key from a public key is computationally unfeasible.
Okay, enough math for now!
Transacting in Bitcoins: The Role of Private Keys
To elucidate the role of private keys in Bitcoin transactions, let's take a representative transaction example involving two parties - Bob and Alice.
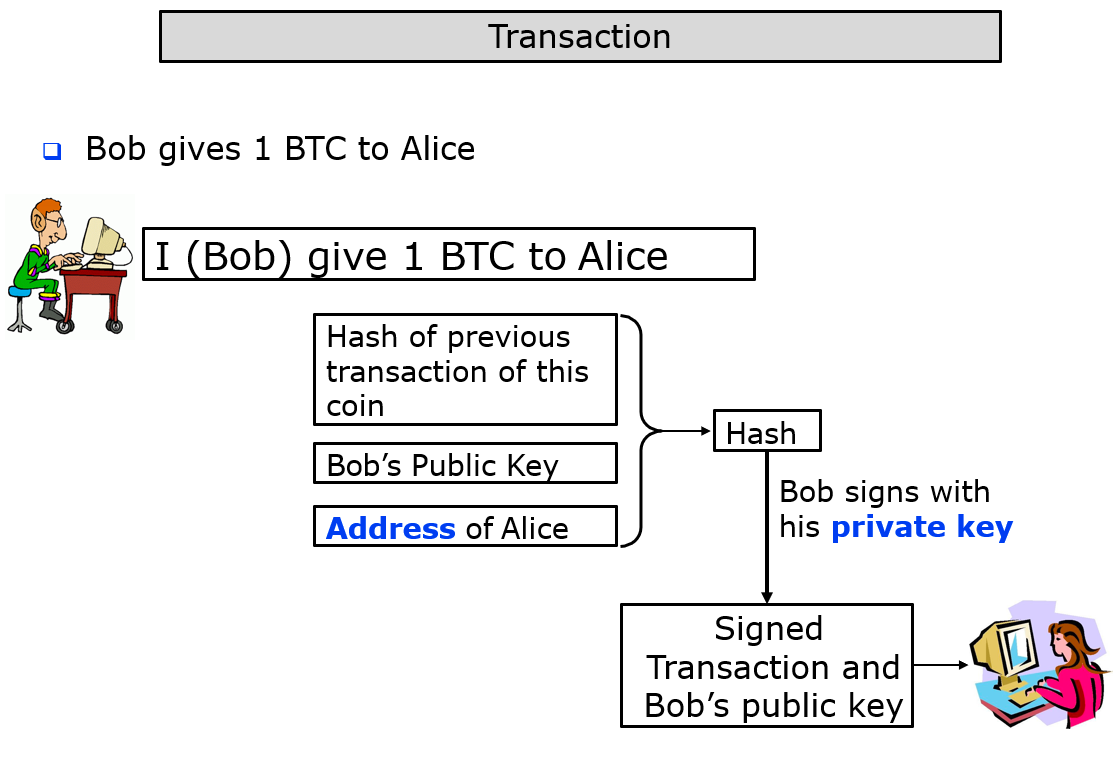
Assume that Bob intends to transfer one bitcoin to Alice. Here's how this transaction would technically unfold:
- Bob initiates the process by accessing his digital Bitcoin wallet. In the wallet's recipient section, he inputs the public key associated with Alice's Bitcoin address.
- The wallet software then constructs a transaction message. This message essentially includes the amount of Bitcoin Bob wants to transfer and Alice's public key. Bob's wallet then signs this transaction using his private key. This signing process involves generating a unique digital signature using cryptographic algorithms (ECDSA).
- Once generated, this digital signature is attached to the transaction. This signature, unique to Bob's private key, is essentially a cryptographic proof that authenticates Bob's ownership of the Bitcoins he's attempting to send.
- This transaction, now bearing Bob's digital signature, is then broadcasted to the Bitcoin network. The nodes within the network validate the transaction by verifying the digital signature using Bob's public key. If the signature corresponds to the transaction message and can be verified with Bob's public key, the network consensus deems the transaction valid.
- After the transaction is verified, the Bitcoin is transferred to Alice's address. At this point, Alice becomes the new owner of the Bitcoin. The access to these funds now depends on the possession of the private key corresponding to Alice's public key (or her Bitcoin address). In this scenario, Alice is the sole possessor of that private key, thereby ensuring she is the only one who can spend the newly acquired Bitcoin.
In essence, this transaction process underscores the pivotal role private keys play in establishing and preserving the security and integrity of Bitcoin transactions.
The Security Imperative: Storing Bitcoin Private Keys
The private key acts as the exclusive gateway to your Bitcoin treasure trove. Thus, its secure storage is non-negotiable. Here are the primary methods:
- Hardware Wallet: This is a tangible device designed to store your private key offline. It's akin to a high-security vault, keeping your key insulated from online threats.
- Software Wallet: This is a software solution that stores your private key on your computer. While it provides quick access, it exposes your key to potential online threats.
- Multi-sig Wallet: This involves multiple keys instead of a single key and requires a quorum of keys to sign a transaction. While it is the safest and most trusted mechanism to store your long term bitcoin stack, it is also very complex to manage multi-sig wallets. Theya simplifies the multi-sig user experience and makes self-custody of private keys mobile-friendly.
Concluding Thoughts
Private keys form the bedrock of Bitcoin's security infrastructure. They're your unique claim to your Bitcoin assets, and their loss could lead to the irreversible loss of your Bitcoins. Hence, secure storage of private keys is paramount.
Here are some best practices:
- Resist the temptation to store your private key online.
- Create a secure backup of your private key and keep it in a safe place.
- Ideally use multi-sig wallets to make avoid single point of failure of losing private keys.
By internalizing these guidelines, you'll fortify your Bitcoin security, providing you with peace of mind. As with any technology, understanding and correctly implementing the fundamentals can go a long way in ensuring a smooth and secure experience.
